Case study: Viral Donald Trump Photo Is Photoshopped
People are posting photoshopped images of Trump again on December 28, 2020. The photograph had been manipulated to make Trump look bigger than he is. An picture of Donald Trump that has been photoshopped to make him look bigger than he really is has gone viral, with many Twitter users posting it as though it were true.
Many people on social media have been spreading the manipulated photo of Donald Trump on their accounts, with the tweet being retweeted or engaged with by more than 3.9K people. AFP/Getty photographer Nicholas Kamm took the original photo on June 28. In the side-by-side comparison, Trump’s appearance has been altered to make his stomach and neck larger in the viral picture. It’s not the first time that photoshopped Trump pictures have gone viral as if they were real. Indeed, there have been a number of controversies over widely circulated photographs of him that were later found to be photoshopped during his four years in presidency.

An account on Twitter named Ken Olin or @kenolin1 is thought to be the person who first spread the manipulated photo of Donald Trump’s appearence which had been altered. Ken Olin tweet the photo with “My god, he’s actually inflating” in Dec 28, 2020 through his Twitter. There are many other twitter account that had been spreading the photo all over the social media with hate quote tweets towards Donald Trump regarding his image.

The perpetrator’s motivation may have been to irritate Trump with the picture that had been distorted or manipulated and for his own entertainment. The perpetrator is unlikely to be a Trump supporter, but he would like all Trump supporters to be enraged by the picture that has gone viral on social media.
There were no significant effects for the victim, Donald Trump. Donald Trump didn’t say anything regarding the viral photo of him being altered an spreaded around the social media. The only effects are that people are talking about his manipulated viral picture, believing it to be real that he had gained weight, and making jokes about his body figure, which leads to body shaming and public shaming of the victim.
No actions were taken by Donald Trump. It is believed that Donald Trump would not really care about the manipulated photo being viral since there are many other problems and work that he needed to focus on. There are some people on social media who reprimand those who mock Trump stating that they not only hurt Trump’s feelings but also the feelings of other fat people as well.

Discussion
Digital Evidence Identification
Digital evidence, also known as electronic evidence, is data or information that resides in a digital format which can be relied on and used in a court of law to prove and expose the truth about a crime. The photo from the phone gallery is one of the most compelling visual proof to prove that a person is sharing manipulated or altered pictures on social media platforms. All of the photos on the phone can be used to show that the phone owner is either storing manipulated pictures on the phone or selecting them directly from the gallery to share on social media platforms.
Following that, browsing history can be considered as yet another piece of compelling digital evidence. This is because it can be used to see if the date of uploading or publishing the altered image on social media matches the date of the user’s account login inside the browser’s history. If both dates are the same, it’s safe to say that the incident of uploading or publishing the altered image on social media was carried out by the account owner rather than by third parties.
Next, social media server logs can be used as digital proof to show that the incident of posting a manipulated image was carried out by a perpetrator. All of the account holder’s social media activity, as well as the IP address, will be documented in the server logs. With the server logs, we can trace the location of the perpetrator when they posted the manipulated photos on their social media.
Furthermore, activity log are also the convincing digital evidence because it can use to check all the activity that being done in the account. Activity log that found from the Twitter setting can be used to check the security and account access. Under the security and account access there’s an apps and sessions where we can see information about when the individual logged into their account and the apps that is connected to that account. Below are an image of session the devices that the individual are using or that have been used before to log in to the twitter account.
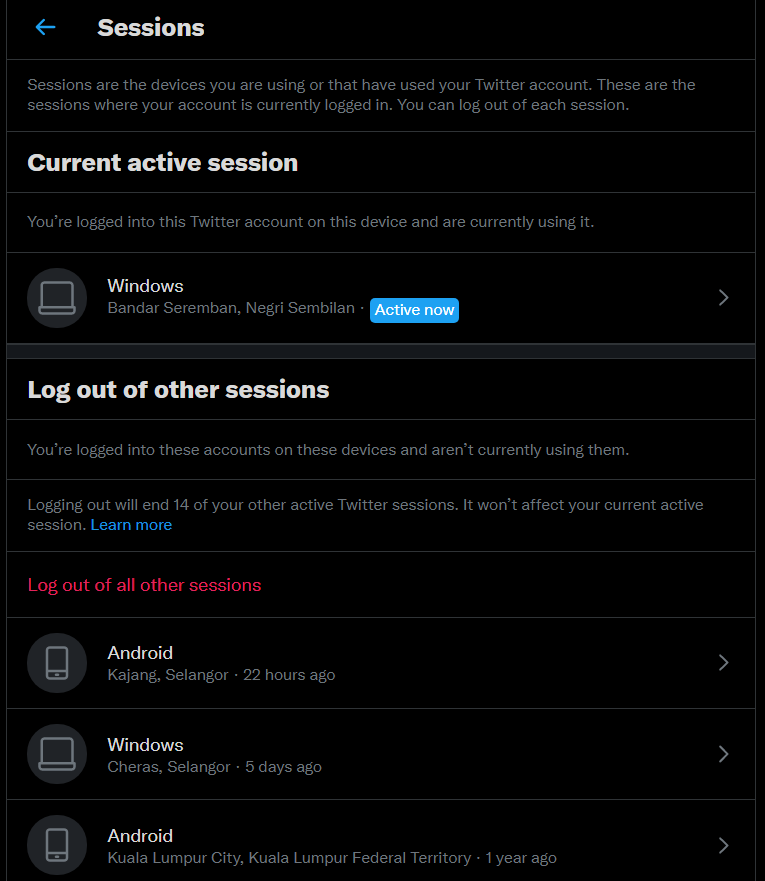
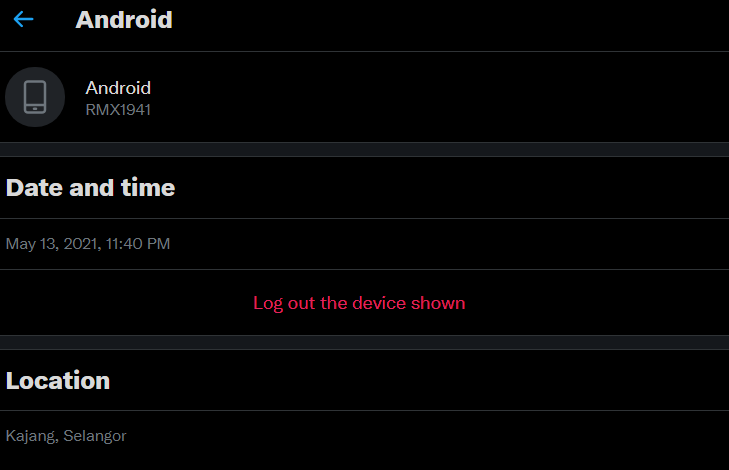
It also shows the date and time that the individual had logged into their account and the location is stated. New possible devices that is being used to login into the account will be directly shown in this section and it can help to warn the user from any unauthorized access. If not new devices is stated, then we can say that all the activities of sharing the manipulated pictures is done by the same person, which is the perpetrator.
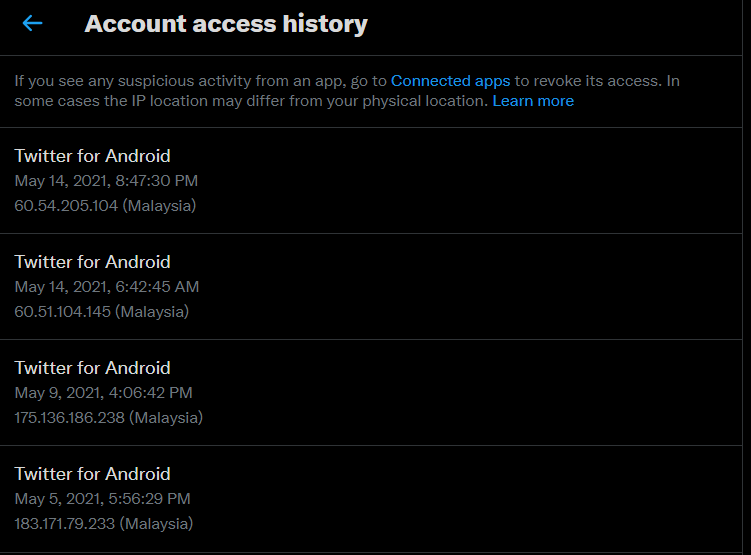
Twitter also provides an account access history when an individual is using the app and the activity shows the IP address when the individual was using their social media. This information can be possible to identify if the perpetrator shared the manipulated images himself or whether his account was compromised by others. If all of the IP addresses in the history are the same, it would be easier to prove that the incident was committed by the individual himself.
Lastly, ISP tracking is also a convincing digital evidence. The internet service provider monitors and logs information about each individual online connection and activity, which can include everything from search history to individual email conversations. ISPs are allowed by law in many parts of the world to keep their customers’ internet data for a certain period of time. This is to allow government security organizations access to the data in the event that it is required as part of an investigation. As a result, the investigator will determine if the incident of sharing or posting manipulated photos on social media was committed by the individual or by others that hacked into the account.
Tool suitable for the case
We can use Forensically, an online platform. Forensically is a free forensic method for digital images. Clone detection, error level analysis, meta data extraction, and several other features are included. We may also use the program when we are not connected to the internet, which is ideal for forensics analysts.
First, it is important to have the original file that had been posted on social media by the perpetrator to know whether the photo had been manipulated or not. Therefore, the photo file that had been uploaded by a twitter account @kenolin1 should be collected. This way the tools are able to detect the manipulated part more correctly.
The forensic analyst should upload or insert the manipulated photo into the forensically tool. The photo is taken from @kenolin1 twitter account post.
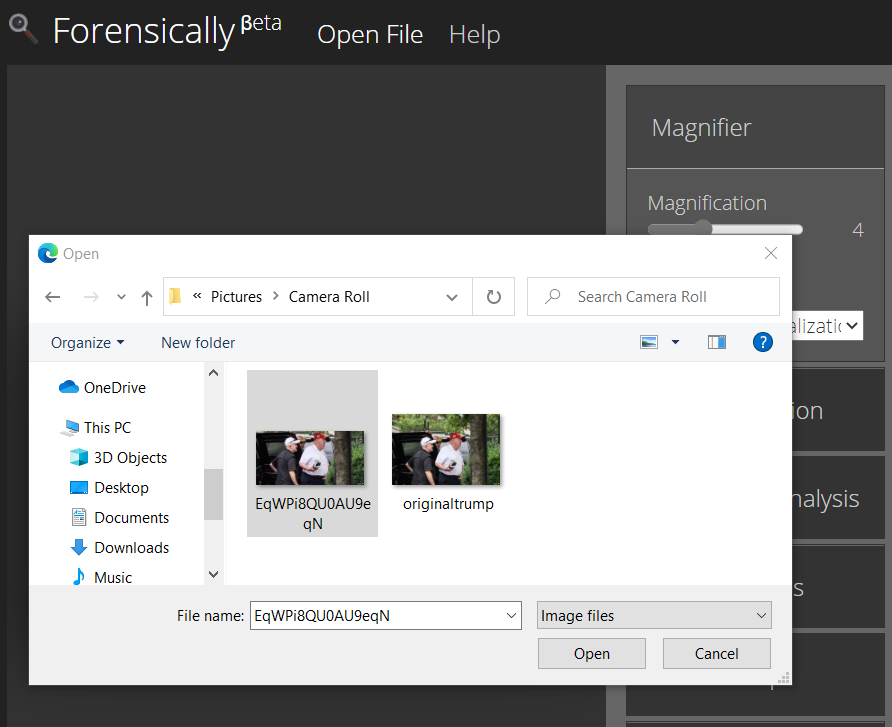
Manipulated image
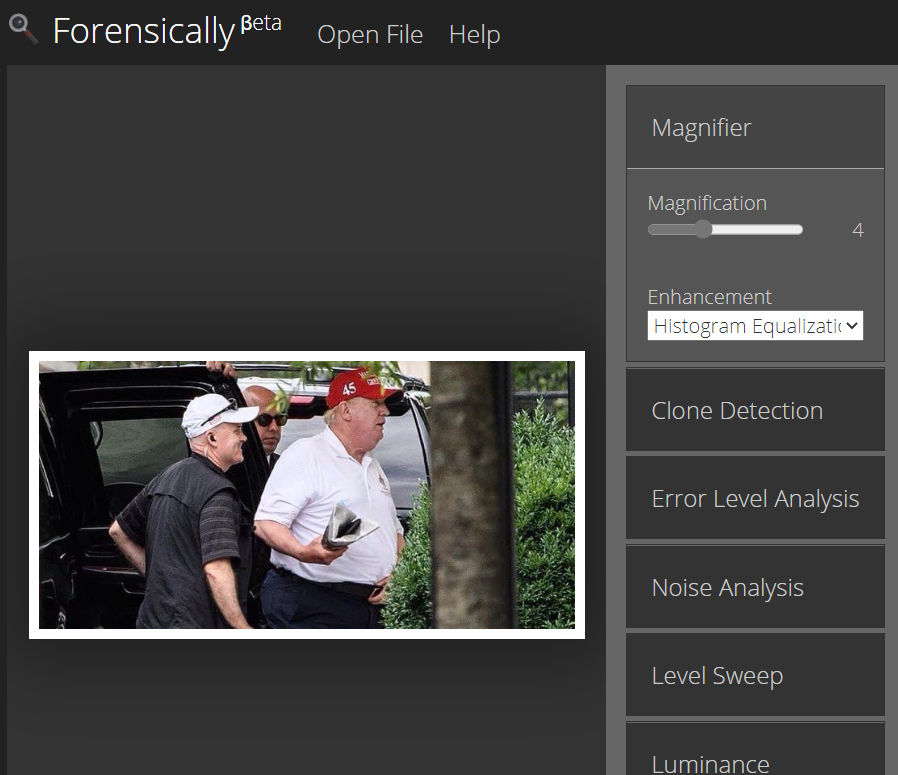
Next, we can use Error Level Analysis tool to examine the image whether it is being manipulated to a recompressed version.
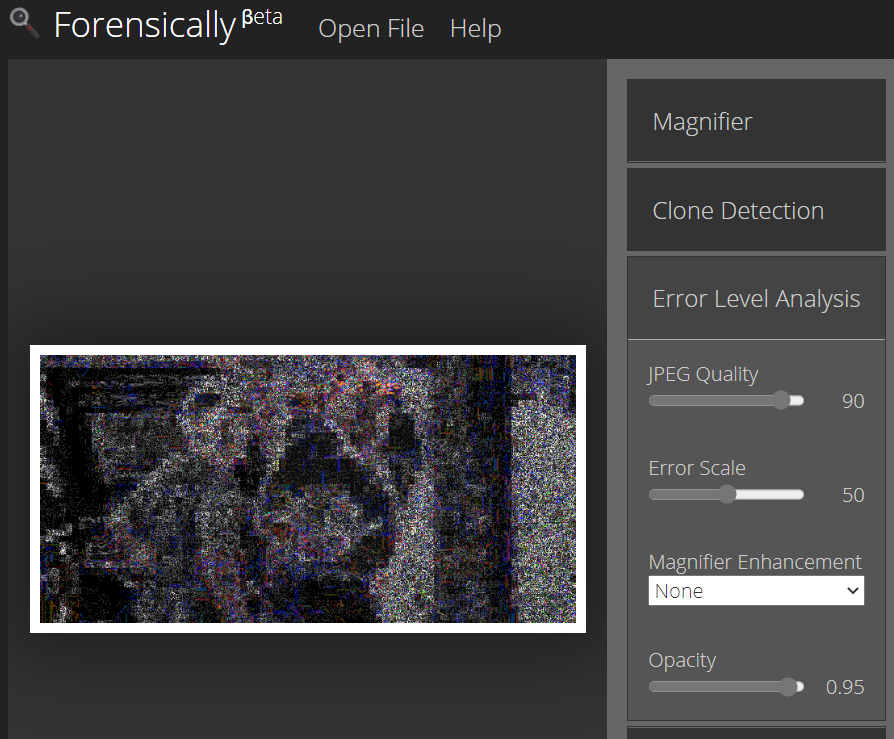
From the manipulated image we can see that Trump clothes are black while around it was white. That means that the clothes is at a different quality level and we can say that the clothes had been modified to make Trump look fat. There are also a large amount of rainbowing in the manipulated image than the original. Photoshop and other Adobe products is said to generate a large amount of rainbowing. Therefore we can say that the image had been manipulated.
Error Level Analysis (Manipulated image)
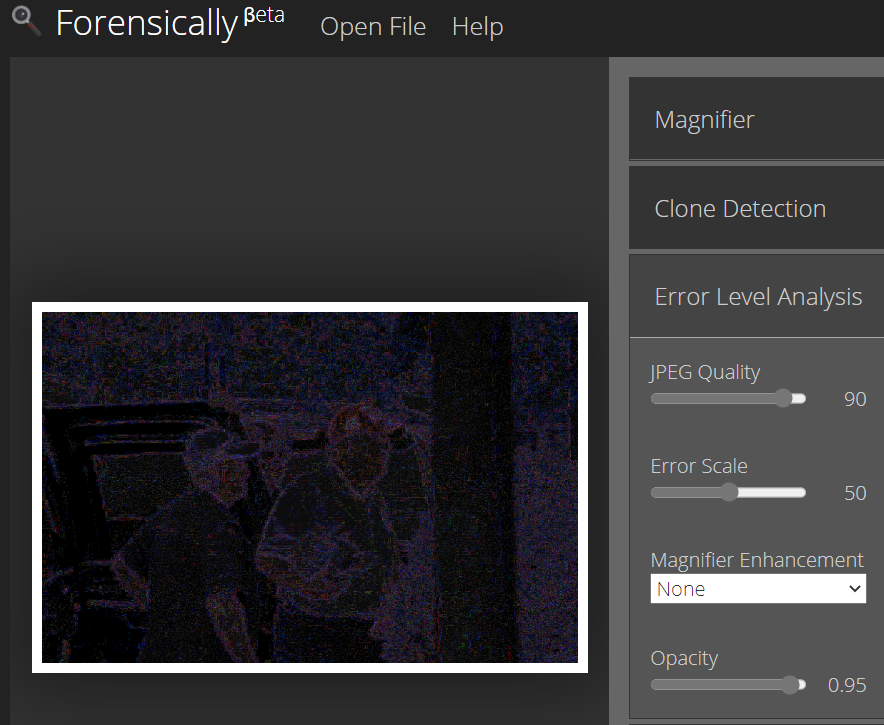
Error Level Analysis (Original image)
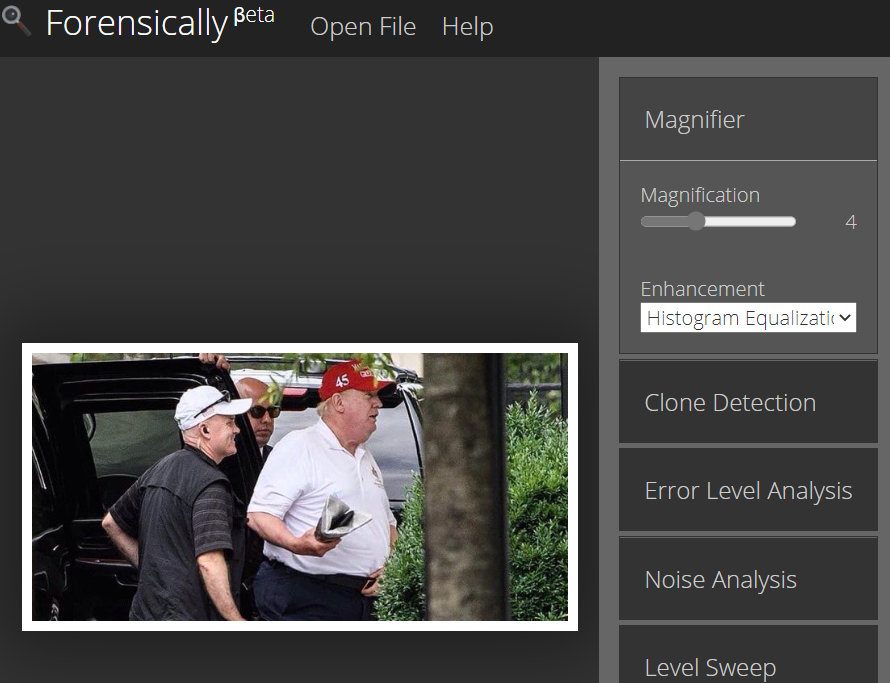
After that, as a forensic analyst we can also use the magnifier to find any differences in the image. Based on the manipulated image below, there are no defects of the image found but we can say the image quality of the manipulated image isn’t a nice quality compared to the original image. From this magnification tool, as a forensic analyst, we can say that the perpetrator are good at altering the photo making it seems true.
Manipulated image
My findings is that we as a forensic analyst can use any tools that is suitable for the graphic analysis to see whether the photo is original and had not been manipulated or not. We should also use different types of tools for us to gather more information regarding the graphic to prove that the perpetrator of this photo manipulation is guilty when we are bringing the evidence to the court. Based on the original photo and the manipulated photo of Trump, we can see that Trump stomach had been exaggerated with editing making his stomach look larger than before.
How to liaise with the Social Media Company
Firstly, since it is a social media companies, we shall need a cooperation with other cybercrime force at that company country to help in searching evidence needed for the case. We can also contact the company itself for the cooperation. We shall need a search warrant issued by the court which is directed to the investigator or a police officer to search the company. After that, we shall evaluate and secure the scene and collect evidence needed for the investigation. During this process we can ask the company to search for posts that had been spread around the social media that can also come with key term or hashtags related with what evidence we are trying to collect. The accounts that had been spreading any manipulated photos, hate comments, posting incriminating content or anything that is related with the case should be also collected as an evidence as this is a proof that these accounts can be the reason that had been affecting the victim. Investigator should also collect hash value that authenticates data and collects all the associated metadata of a social media post that can be used in court. To stop the attack, the company should work together with the forensic or the investigator team to remove all content that is related with the attack to stop it from spreading all around the social media and terminate or remove the accounts that had been spreading it.
Artifacts (Evidence & Resources)
- People Are Sharing Photoshopped Pictures of Trump – Again
Ellie Hall (2020, Dec 29)
“Fat” Viral Donald Trump Photo Is Photoshopped (buzzfeednews.com)
The report is talking about the doctored image that makes Trump appear larger than his actual size on social media. - Forensically, free online photo forensic tools
Forensically, free online photo forensics tools – 29a.ch
This website is an online free photo forensic tools that can be used by a forensic analyst to determine whether the image had been manipulated or not. - What Is ISP Tracking and How Can You Prevent It?
Tim Mocan (2018, Sep 18)
What Is ISP Tracking (and How Can You Block It)? | CactusVPN
Explanation about the ISP tracking and why ISP tracking is tracking the users’. - FotoForensic (Error Level Analysis)
FotoForensics
Explation and tutorial of error level analysis tools to detect the manipulated part of the image.